Advanced DDoS Protection
A Distributed Denial of Service (DDoS) attack aims to overwhelm websites and platforms with malicious traffic, making them slow or even unavailable. Beyond the financial impact, this type of threat can seriously damage your company’s reputation.
With this in mind, all our servers and services come with built-in Anti-DDoS protection at no additional cost. Our infrastructure is designed to filter malicious traffic across multiple layers — from the network edge to the data centers — ensuring the continuity of your services.
With mitigation capacity measured in terabits per second, we offer proven resilience even against large-scale attacks, guaranteeing stability and trust for your business.
Simple and Intelligent
All L2JCENTER services already come with Anti-DDoS protection enabled by default. If you need additional configurations, you can easily customize the protection rules in the control panel.
Global Presence
L2JCENTER operates on a robust, globally distributed network with enough throughput capacity to mitigate attacks from any origin. This ensures your services remain available and stable, even during an active attack.
Guaranteed Savings
No matter the size of your project — from a simple personal site to a complete corporate infrastructure — everyone benefits from Anti-DDoS protection at no extra cost. You don’t need to invest in additional resources to maintain service quality: our mitigation kicks in within seconds.
Get the best out of our Anti-DDoS infrastructure
The L2JCENTER Anti-DDoS solution consists of:
More than 17 Tbit/s of capacity for filtering global attacks
Active detection and real-time mitigation against malicious traffic
Unlimited protection at no extra cost, regardless of attack volume
Continuous defense: your protection lasts as long as the attack is active
Our protection also guarantees:
Proven experience in defending different services, from small websites and DNS to large cloud platforms.
High performance, with the best hardware and software solutions in the category.
Data sovereignty, ensuring that your traffic is not shared with third parties.
Total flexibility, with customized protection rules to meet your specific needs.

Guidelines for Mitigating DDoS Attacks
Are you prepared for a DDoS attack? Be proactive and strengthen your infrastructure with advanced firewall rules at the network edge. This way, you reduce server overload and ensure greater stability during high-traffic incidents.
The rules can be applied directly to your IP — just read our guide on how to do it or contact one of our specialists for the necessary guidance.
Multi-Layered Defense System
To deliver the highest quality in network traffic filtering with the lowest possible latency impact, our infrastructure divides each mitigation stage into different layers. Each module has a specific function and applies its own techniques, ensuring complete and efficient protection.
At L2JCENTER, we use cutting-edge hardware and software technologies to guarantee that our clients always experience the best performance, even in high-volume attack scenarios.
Smart, fast, and scalable protection — ready to act in any situation.

Advanced Application Layer Protections
In many cases, generic network protection is not enough. This is even more critical in environments like web and gaming, which are among the most common targets of application-level attacks.
In these situations, attackers exploit vulnerabilities directly in the application logic, making the attack invisible to traditional firewalls.
At L2JCENTER, we offer specialized solutions that go beyond basic protection, ensuring reinforced security for your services and applications at all levels.
Discover our advanced protection products and keep your business always available.
Frequently Asked Questions
Digital security involves different types of threats, and DDoS attacks can take many forms, changing in intensity and technique over time. L2JCENTER’s Anti-DDoS infrastructure is designed to handle the most common and dangerous vectors, including:
Distributed Denial of Service (DDoS) attacks: when thousands of machines try to overload your server at the same time.
Packet floods: mass sending of packets to consume bandwidth and processing power.
SYN Floods: attacks that exploit the TCP protocol to exhaust the server’s connection resources.
Spoofing: when the attacker forges IP addresses to disguise the traffic’s origin.
Malformed or amplification attacks: exploit protocol flaws or misconfigured services to multiply the attack volume.
These types of attacks cannot be blocked by local measures alone, since malicious traffic can saturate the network link before even reaching your server. That’s why L2JCENTER implements protection directly at the network layer, ensuring filtering and mitigation before the attack impacts your services.
All L2JCENTER services and solutions come with integrated Anti-DDoS protection. This defense operates directly at the network edge as well as within our core infrastructure, ensuring that any resource exposed to the internet is protected against malicious traffic.
This means that whether you are a client of dedicated servers, VPS, gaming services, or web applications, all communication passes through our mitigation system before reaching its final destination. As a result, your application remains available and secure even during attack attempts.
The likelihood of suffering a DDoS attack today is high and very common, affecting everything from small websites to large platforms. Without proper protection, your server could become unavailable within minutes, causing slowness, access failures, and even loss of clients.
With L2JCENTER’s Anti-DDoS infrastructure, all traffic first passes through detection and filtering systems distributed across our network. This ensures that legitimate access continues to flow normally while malicious traffic is blocked in real time.
This way, you keep your services stable, fast, and always available — even during massive attacks.
Yes. The L2JCENTER system has full-time active detection. This means all network traffic is continuously monitored.
When suspicious behavior is identified, protection automatically switches into mitigation mode, where deeper analysis is performed, and specific filters are applied to neutralize the attack.
As soon as traffic returns to normal, mitigation is deactivated and your connection continues operating without additional blocks — but the system always remains on alert, ready to act immediately against any new attack attempt.
No. L2JCENTER’s Anti-DDoS infrastructure offers continuous and unlimited protection, regardless of how many attacks your services may face throughout the month.
Whether it’s a single isolated attack or multiple successive attempts, our network is prepared to detect, filter, and mitigate without restrictions or additional charges. The goal is to ensure the full availability of your services, without you having to worry about limits or interruptions.
No. L2JCENTER’s Anti-DDoS infrastructure does not impose traffic limits for mitigation. Even during high-volume attacks, our system continues filtering and blocking malicious traffic without interruptions.
This means that regardless of the intensity or duration of the attack, your services remain protected, with no risk of the defense “shutting down” due to hitting any technical or bandwidth limit.
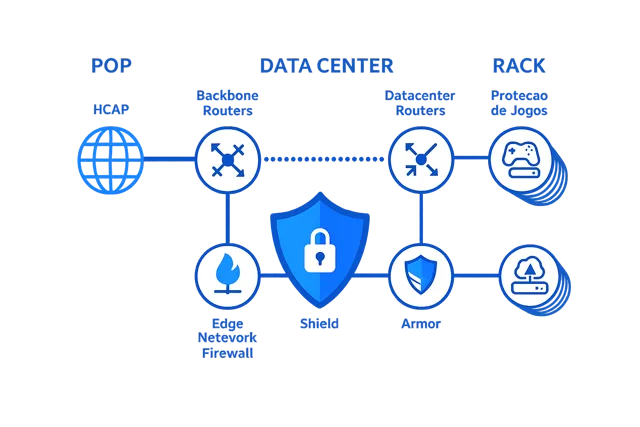
VAC is one of the core components of the Anti-DDoS infrastructure at the datacenter we work with. It combines various filtering and traffic analysis technologies that are constantly evolving to identify and block DDoS attacks in real time.
In practice, VAC inspects all incoming traffic and ensures that only legitimate packets reach your server, while malicious traffic is automatically discarded.
Among the features that make up VAC are:
Edge Firewall: the first barrier against suspicious traffic.
Shield: a specialized layer to absorb and neutralize volumetric attacks.
Armor: an advanced module for more complex attacks, such as protocol exploitation and application-layer threats.
This way, a multi-layered defense is provided, combining performance with high-level security.
